
Today is Father’s day. Your organization purchased a batch of high-end laptops as gifts for winners of Father of the year. When evaluating the procurement business case, which of the following is most suitable for providing security assurance of the operating system and application software preinstalled on those laptops? (Wentz QOTD)
A. TCSEC
B. CMMI
C. SOC 2 Type II
D. Common Criteria
Kindly be reminded that the suggested answer is for your reference only. It doesn’t matter whether you have the right or wrong answer. What really matters is your reasoning process and justifications.
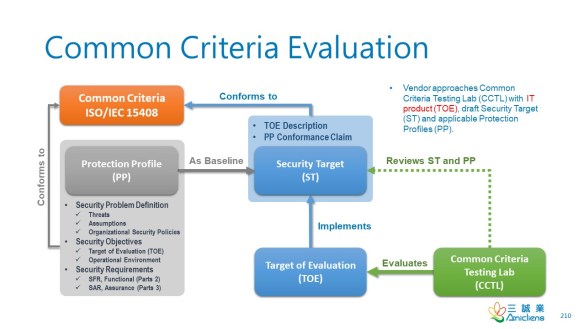
My suggested answer is D. Common Criteria.
Wentz’s book, The Effective CISSP: Security and Risk Management, helps CISSP and CISM aspirants build a solid conceptual security model. It is a tutorial for information security and a supplement to the official study guides for the CISSP and CISM exams and an informative reference for security professionals.
TCSEC is used in DoD to evaluate trusted computer systems. It applies to a computer system as a whole, not to specific software components. Besides, it’s obsolete.
Trusted Computer System Evaluation Criteria (TCSEC) is a United States Government Department of Defense (DoD) standard that sets basic requirements for assessing the effectiveness of computer security controls built into a computer system. The TCSEC was used to evaluate, classify, and select computer systems being considered for the processing, storage, and retrieval of sensitive or classified information. (Wikipedia)
CMMI is a process-based model used to evaluate an organization’s capability maturity of software development, acquisition, or service delivery. It doesn’t apply to the software itself.
SOC 2 Type II is a report on controls at a service organization relevant to security, availability, processing integrity, confidentiality, or privacy. These reports are intended to meet the needs of a broad range of users that need detailed information and assurance about the controls at a service organization relevant to security, availability, and processing integrity of the systems the service organization uses to process users’ data and the confidentiality and privacy of the information processed by these systems. (AICPA)
Reference
- Approved Protection Profiles
- Certified Products
- Windows 10: build 10.0.15063 (also known as version 1703)
今天是父親節。 您的組織購買了一批高端筆記本電腦作為禮物送給榮獲年度父親奬的員工。 在評估採購業務案例(business case)時,以下哪項最適合為筆記本電腦上預裝的操作系統和應用軟件提供安全保證(security assurance)? (Wentz QOTD)
A. TCSEC
B. CMMI
C. SOC 2 Type II
D. Common Criteria

Pingback: 系統和應用軟體提供安全保證- 通用標準(Common Criteria) – Choson資安大小事