
The Extensible Authentication Protocol (EAP) is not a wire protocol; instead, it only defines message formats and typically runs directly over data link layers. Which of the following protocols is not used to encapsulate EAP messages?
A. PPP (Point-to-Point Protocol)
B. PEAP (Protected Extensible Authentication Protocol)
C. LEAP (Lightweight Extensible Authentication Protocol)
D. EAPoL (EAP over LAN)
Kindly be reminded that the suggested answer is for your reference only. It doesn’t matter whether you have the right or wrong answer. What really matters is your reasoning process and justifications.
My suggested answer is C. LEAP (Lightweight Extensible Authentication Protocol).
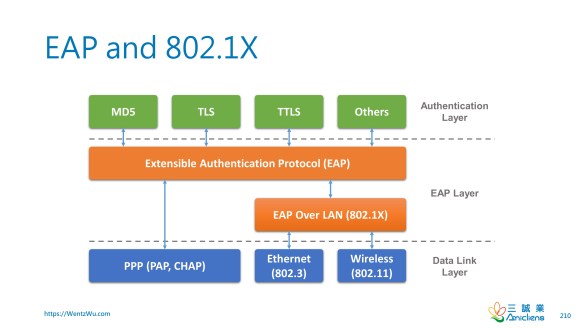
The following is an excerpt from Wikipedia:
EAP is not a wire protocol; instead it only defines message formats. Each protocol that uses EAP defines a way to encapsulate EAP messages within that protocol’s messages.
- IEEE 802.1X: The encapsulation of EAP over IEEE 802 is defined in IEEE 802.1X and known as “EAP over LANs” or EAPOL. EAPOL was originally designed for IEEE 802.3 ethernet in 802.1X-2001, but was clarified to suit other IEEE 802 LAN technologies such as IEEE 802.11 wireless and Fiber Distributed Data Interface (ANSI X3T9.5/X3T12, adopted as ISO 9314) in 802.1X-2004. The EAPOL protocol was also modified for use with IEEE 802.1AE (MACsec) and IEEE 802.1AR (Initial Device Identity, IDevID) in 802.1X-2010.
- PEAP: The Protected Extensible Authentication Protocol, also known as Protected EAP or simply PEAP, is a protocol that encapsulates EAP within a potentially encrypted and authenticated Transport Layer Security (TLS) tunnel. The purpose was to correct deficiencies in EAP; EAP assumed a protected communication channel, such as that provided by physical security, so facilities for protection of the EAP conversation were not provided.
- RADIUS and Diameter
- PANA (Protocol for Carrying Authentication for Network Access)
- PPP: EAP was originally an authentication extension for the Point-to-Point Protocol (PPP). PPP has supported EAP since EAP was created as an alternative to the Challenge-Handshake Authentication Protocol (CHAP) and the Password Authentication Protocol (PAP), which were eventually incorporated into EAP. The EAP extension to PPP was first defined in RFC 2284, now obsoleted by RFC 3748.
LEAP and 802.1X
Rakhi Gupta asked about LEAP and 802.1X as follows:
Hello sir. Need a clarification. I understand that EAP is a framework that is used by Authenticator to request for identity and credentials and notify the authentication outcome whereas 802.1x is the protocol used for network access control. I was trying to understand why LEAP does not use EAP for encapsulation as per one of your QoD, is it because it directly uses authentication mechanism? Some of the books like CBK and Shon Harris have text that is confusing and they seem to be indicating that LEAP also uses EAP framework.
LEAP is a legacy protocol developed by Cisco before 802.11i was approved. It uses a modified version of MS-CHAP. As it is built upon the EAP framework, we can treat it as a standard EAP authentication protocol, just like CHAP in PPP. In summary, LEAP relies on EAP; it doesn’t encapsulate EAP.
802.1X is all about sending EAP over LAN. In other words, it’s about how to encapsulate EAP messages in Ethernet or Wireless frames so that LAN connections can be authenticated.
More on PEAP
However, Microsoft PEAP builds a TLS tunnel to enhance the security of the native EAP, designed with the assumption that the circuit is secure and with no extra security protection. It establishes a TLS tunnel in phase 1 while encapsulates other EAP authentication protocols in phase 2.
The following diagram demonstrates how PEAP encapsulates EAP messages in phase 2. Please refer to MS-PEAP for details.

Reference
- Extensible Authentication Protocol
- Extensible Authentication Protocol (EAP)
- PPP Extensible Authentication Protocol (EAP)
- PPP Authentication Protocols
- [MS-PEAP]: Protected Extensible Authentication Protocol (PEAP)
- Cisco LEAP
A BLUEPRINT FOR YOUR SUCCESS IN CISSP
My new book, The Effective CISSP: Security and Risk Management, helps CISSP aspirants build a solid conceptual security model. It is not only a tutorial for information security but also a study guide for the CISSP exam and an informative reference for security professionals.
- It is available on Amazon.
- Readers from countries or regions not supported by Amazon can get your copy from the author’s web site.
可擴展身份驗證協議(EAP)不是線路(wire)的協議。 相反地,它僅定義訊息格式,而且通常直接在數據鏈路(daya link)層上運行。 以下哪一項協議沒有用來封裝EAP訊息?
A. PPP (Point-to-Point Protocol)
B. PEAP (Protected Extensible Authentication Protocol)
C. LEAP (Lightweight Extensible Authentication Protocol)
D. EAPoL (EAP over LAN)
